N
Nedim
Guest
IIS uses bindings to determine where to redirect requests. These bindings can be secured (https – mostly on port 443) or unsecured (http – mostly on 80).
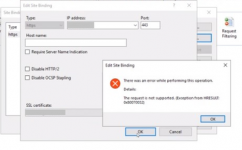
In a case I worked on, I came across to this error while trying to add an https binding: The request is not supported (Exception from HRESULT: 0x80070032).
The PowerShell command below gave an error too
netsh http add sslcert ipport=[IP ort] appid="[APP ID]" certhash=[HASH] certstorename=MY
ort] appid="[APP ID]" certhash=[HASH] certstorename=MY
SSL Certificate add failed, Error: 50
The request is not supported

Additionally, Windows Update wasn’t working neither. It displayed the following error.
“We couldn’t connect to the update service. We’ll try again later, or you can check now.”
Solution
Since both secure binding and Windows Update were failing, the issue seemed to be related to TLS protocol settings.
If you are troubleshooting a similar issue, make sure TLS protocols and encryption algorithms are enabled. Additionally, check if secure cipher suites are enabled. In our case, there was only one cipher suite defined. This was the reason of both binding and Windows Update issues.
We followed the steps below to use default cipher suite list:
Continue reading...
In a case I worked on, I came across to this error while trying to add an https binding: The request is not supported (Exception from HRESULT: 0x80070032).

The PowerShell command below gave an error too
netsh http add sslcert ipport=[IP
SSL Certificate add failed, Error: 50
The request is not supported
Additionally, Windows Update wasn’t working neither. It displayed the following error.
“We couldn’t connect to the update service. We’ll try again later, or you can check now.”
Solution
Since both secure binding and Windows Update were failing, the issue seemed to be related to TLS protocol settings.
If you are troubleshooting a similar issue, make sure TLS protocols and encryption algorithms are enabled. Additionally, check if secure cipher suites are enabled. In our case, there was only one cipher suite defined. This was the reason of both binding and Windows Update issues.
We followed the steps below to use default cipher suite list:
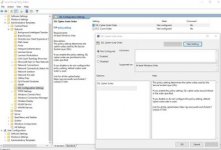
- Go to “Start > Run“. Enter: gpedit.msc
- In the left pane, expand “Computer Configuration > Administrative Templates > Network > SSL Configuration Settings“
- In the right pane, right click “SSL Cipher Suite Order” and choose “Edit”
- Save the text inside “SSL Chiper Suite” field to a Notepad for backup
- Select “Not Configured”
- Click “OK”
- Restart the server (gpupdate doesn’t enforce this setting. You should restart the server)

Continue reading...